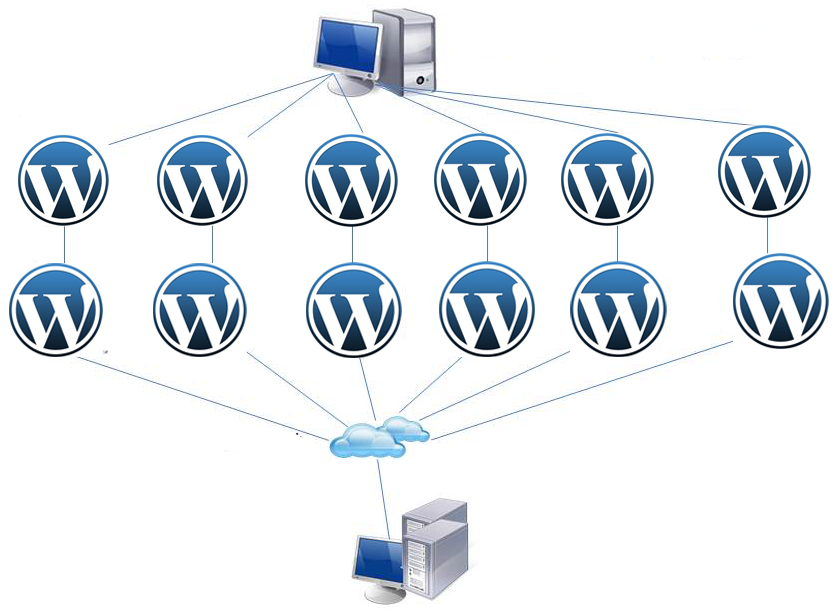
 Technical representative of Sucuri, Daniel Cid says that DDos attacks have started against one of the popular WordPress websites, and when the number of attacks are increasing, a side, which provides a host service, has stopped their site activity. Researchers have shown that, it is the large scale “HTTP-flood Layer 7” attack and it realizes sending hundreds of request to their server. During a few hours, as a result of the attacks from more than 162 websites in Wordpress, this site has been suspended. Researchers have shown that, sites which participated in the attacks, was used as a botnet by hackers. The reason of these sites being a member of botnet, is sending Pingback request to the *XML-RPC file of WordPress, and it is possible to realize attack as a result of a simple Linux command. It may be concluded that, through any WordPress site, which **PingBack parameter is active, is possible to realize DDos attacks. So, PingBack parameter becomes active in the WordPress sites by default. To prevent your WordPress sites against these attacks, you can find the recommendations from here, prepared by The Cyber Security Center.
Technical representative of Sucuri, Daniel Cid says that DDos attacks have started against one of the popular WordPress websites, and when the number of attacks are increasing, a side, which provides a host service, has stopped their site activity. Researchers have shown that, it is the large scale “HTTP-flood Layer 7” attack and it realizes sending hundreds of request to their server. During a few hours, as a result of the attacks from more than 162 websites in Wordpress, this site has been suspended. Researchers have shown that, sites which participated in the attacks, was used as a botnet by hackers. The reason of these sites being a member of botnet, is sending Pingback request to the *XML-RPC file of WordPress, and it is possible to realize attack as a result of a simple Linux command. It may be concluded that, through any WordPress site, which **PingBack parameter is active, is possible to realize DDos attacks. So, PingBack parameter becomes active in the WordPress sites by default. To prevent your WordPress sites against these attacks, you can find the recommendations from here, prepared by The Cyber Security Center.
*XML – RPC is a remote procedure call protocol which uses XML to encode its calls and HTTP as a transport mechanism
**PingBack –A pingback is one of three types of linkback methods for Web authors to request notification when somebody links to one of their documents.Linkback has 4 types ping-back, refback, trackback, webmention.



