 Over one million PCs compromised by Win32.Sector file infector. Win32.Sector is a complex polymorphic malicious program that can spread on its own (without user intervention) and infect files. Its main function is to download various executables via P2P networks and run them on infected machines. This malicious program can inject its code into running processes, terminate certain anti-viruses and block access to the sites of their respective developers. Win32.Sector can infect files on local and removable disks (in the latter case, it can create the file autorun.inf on removable media) as well as in shared network folders. By design, Win32.Sector has no control servers; instead it connects with other bots running on infected machines. It determines whether the computer has an external IP address or connects to a network that uses NAT. When launched on an infected computer, Win32.Sector uses an initial list of IP addresses to connect to other bots. If successful, the file infector executes the following commands:
Over one million PCs compromised by Win32.Sector file infector. Win32.Sector is a complex polymorphic malicious program that can spread on its own (without user intervention) and infect files. Its main function is to download various executables via P2P networks and run them on infected machines. This malicious program can inject its code into running processes, terminate certain anti-viruses and block access to the sites of their respective developers. Win32.Sector can infect files on local and removable disks (in the latter case, it can create the file autorun.inf on removable media) as well as in shared network folders. By design, Win32.Sector has no control servers; instead it connects with other bots running on infected machines. It determines whether the computer has an external IP address or connects to a network that uses NAT. When launched on an infected computer, Win32.Sector uses an initial list of IP addresses to connect to other bots. If successful, the file infector executes the following commands:
Use a download link to request a configuration file via UDP;
Request plugins (via TCP);
Check for NAT; if unavailable, the bot receives a unique identification number ID (via UDP);
Obtain the IP address of another infected machine to establish a connection (via UDP);
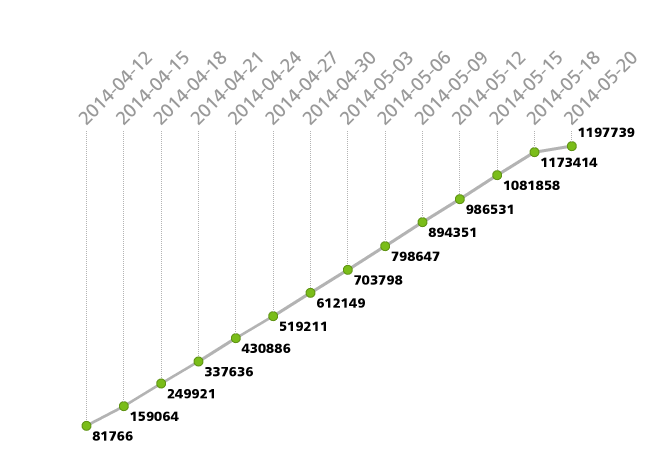
Sector botnet was comprised of 1,197,739 unique bots, 109,783 of which had external IP addresses and could operate routers for other infected hosts.
Source: www.Drweb.com



