More than 162 thousands sites which based on WordPress are used for large-scale DDos attacks. Cyber Security Center has made recommendations, for eliminating these vulnerabilities which caused these attacks, and preventing them.
As a result of investigations about sites, which took part in attacks and how enter bootnet, it was revealed that, it is possible to do DDos attack through any WordPress site, in which Pingback parameter is active. Thus, the Pingback parameter becomes active in WordPress sites. If this parameter is not necessary to use, it is recommended to deactivate it
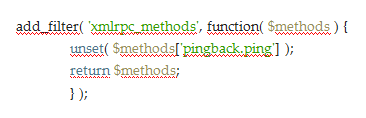
The best way to do this is to deactivate plug-in through the following codes. If you want to determine that your WordPress site participate or not participate in these attacks, you can benefit from recommendations made for technical administrator and site owners.
For technical administrators:
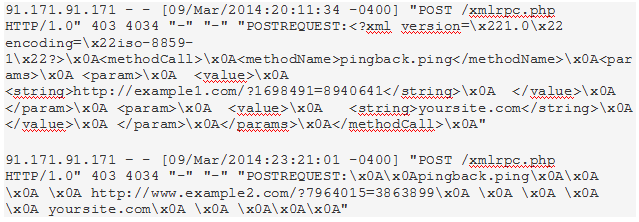
In order to determine that your website participate or not participate in these attacks look at any POST request in XML-RPC file in log records. If there is any Pingback in URL address, so your site is used in attacks. For example, if we look at the picture in the following example, see that site was used implementations of DDos attacks to www.example1.com and www.example2.com sites.
For owners of internet resources:
Taking into account the scale of the spread of problem, Sucuri company produced the scanner for site owners which determine the using of the sites in attacks. This scanner is named WordPress DDos Scanner. You can access this page, write the address of your site and check it.



